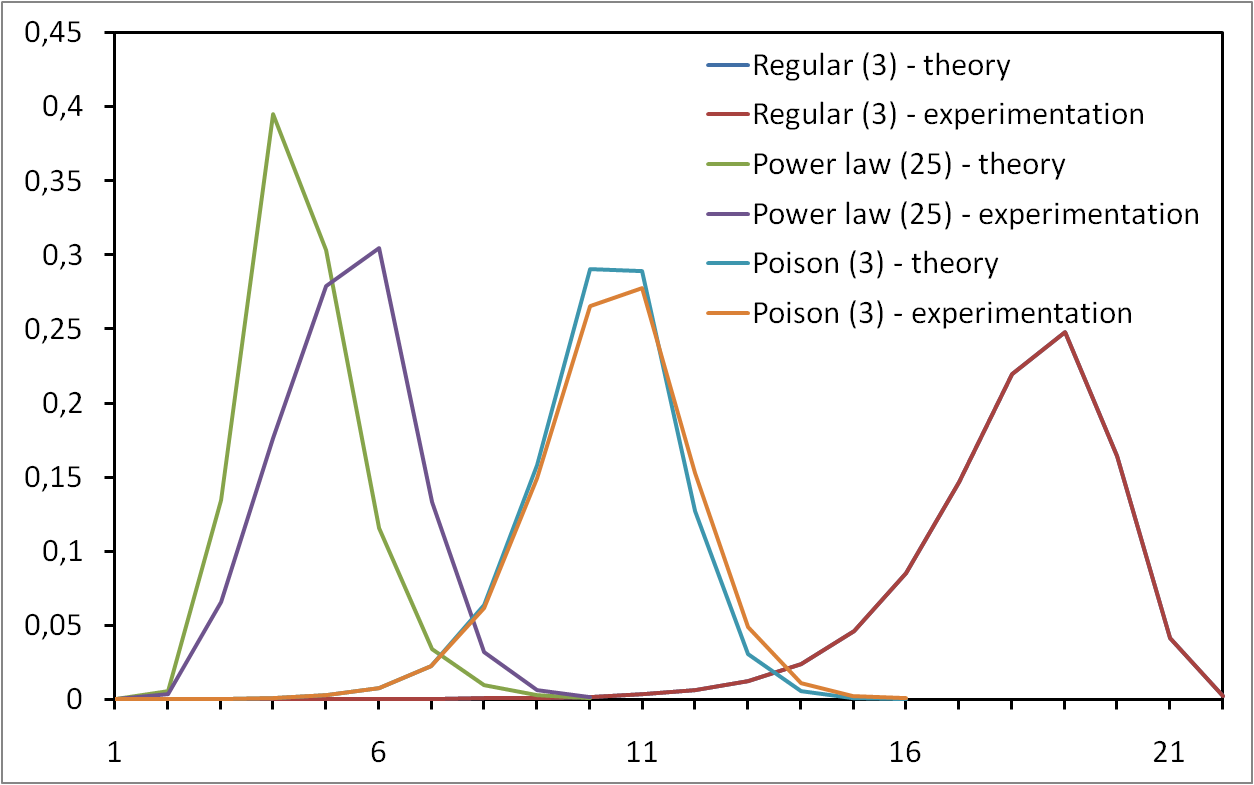
Interval between the discoveries of IP addresses from several monitors
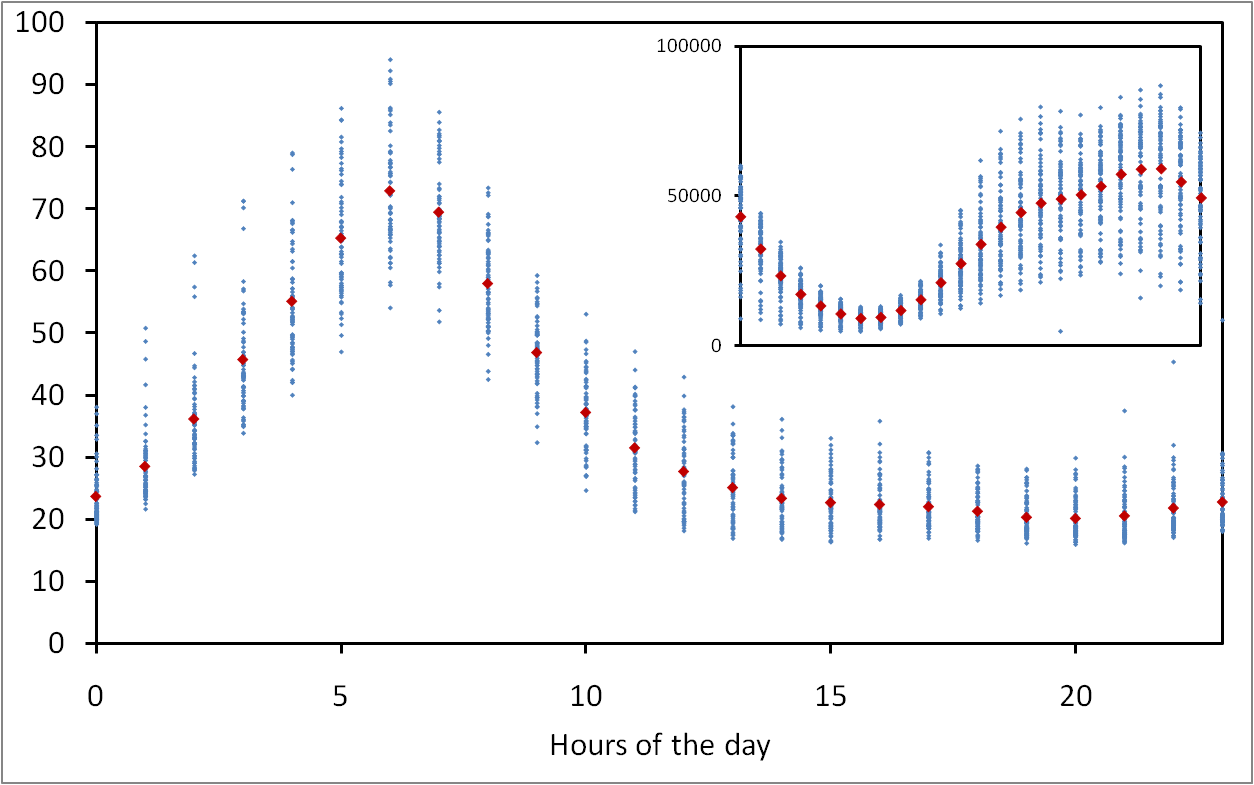
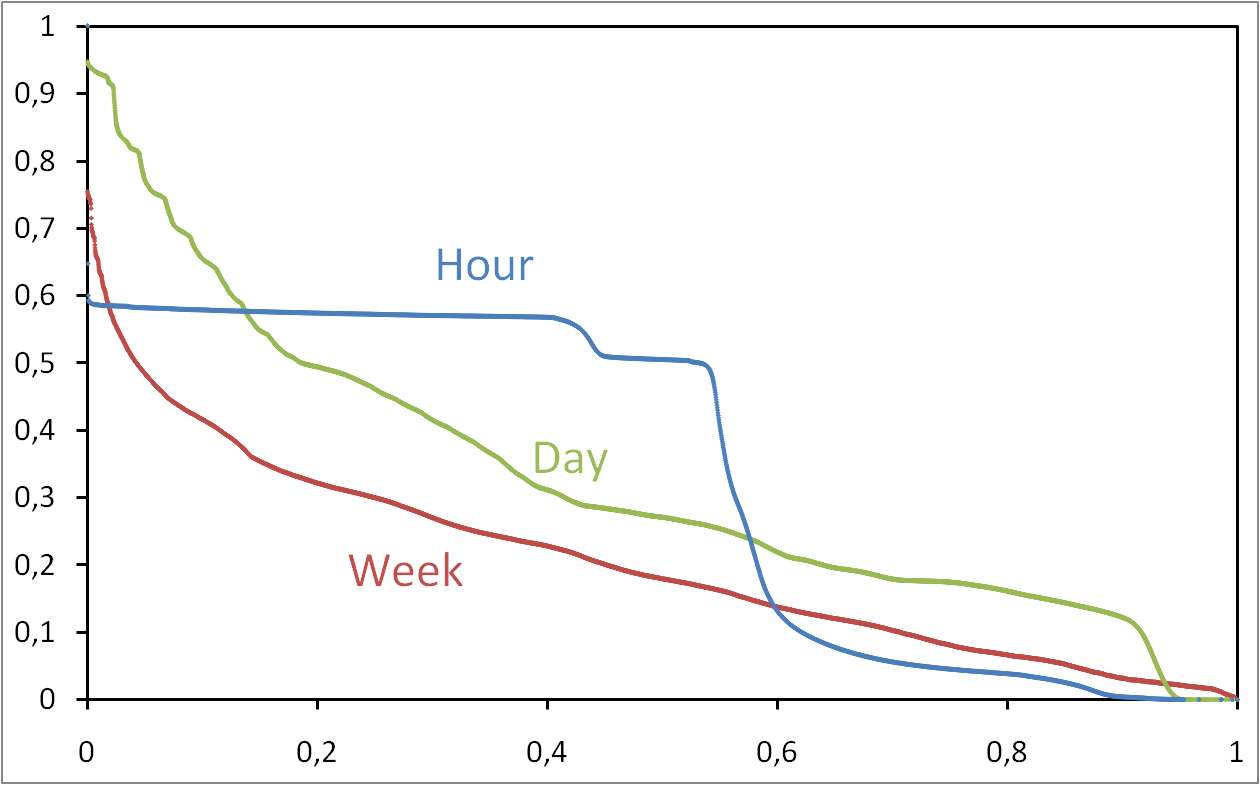
Typical days of search management for an eDonkey server
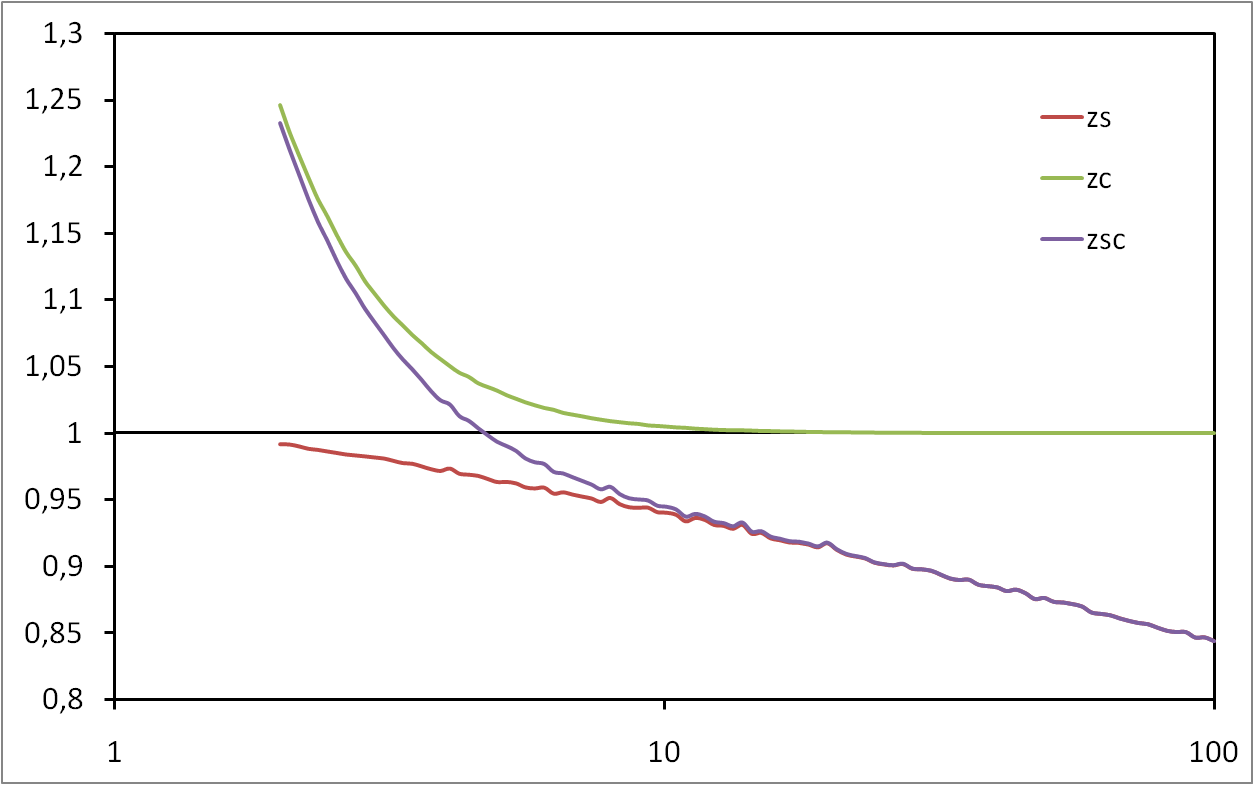
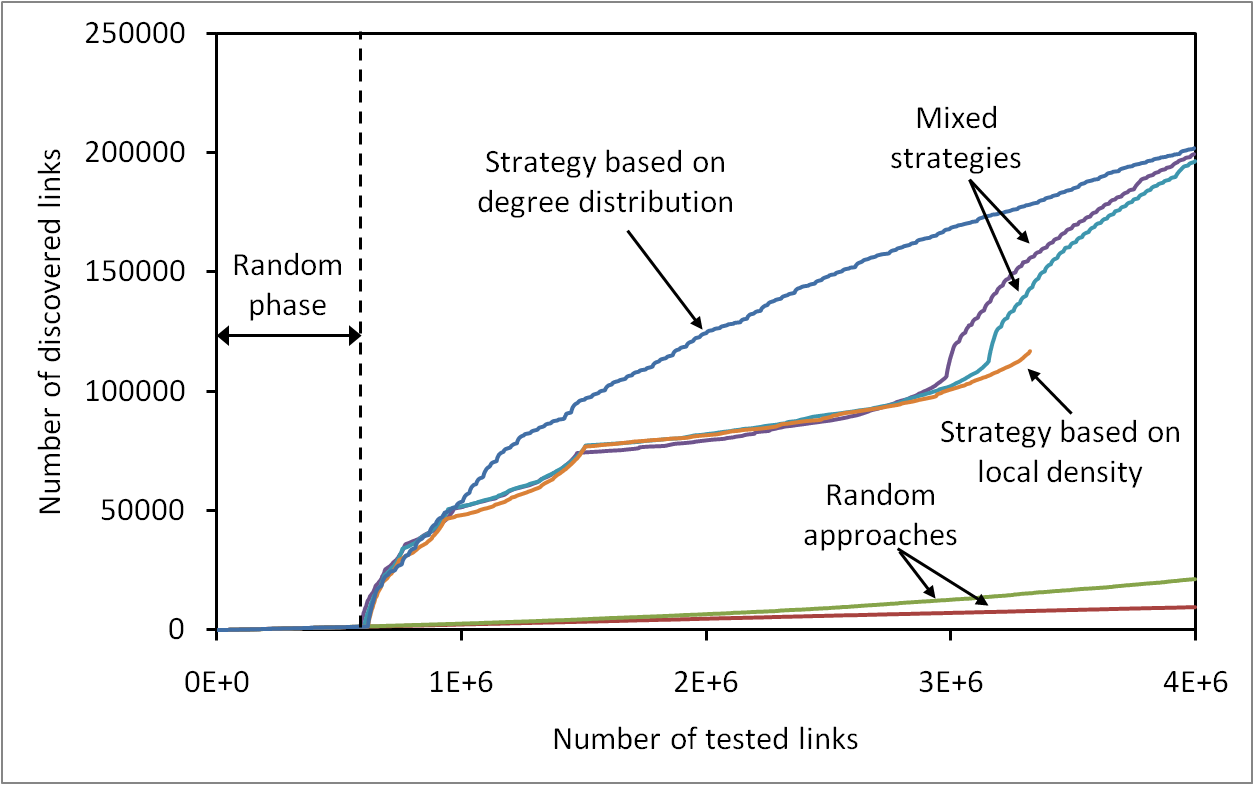
Efficient Measurement of Complex Networks Using Link Queries
Fabien Tarissan, Matthieu Latapy and Christophe Prieur
In Proceedings of the IEEE International Workshop on Network Science For Communication Networks (NetSciCom’09)
Complex networks are at the core of an intense research activity. However, in most cases, intricate and costly measurement procedures are needed to explore their structure. In some cases, these measurements rely on link queries: given two nodes, it is possible to test the existence of a link between them. These tests may be costly, and thus minimizing their number while maximizing the number of discovered links is a key issue. This is a challenging task, though, as initially no information is known on the network. This paper studies this problem: we observe that properties classically observed on real-world complex networks give hints for their efficient measurement; we derive simple principles and several measurement strategies based on this, and experimentally evaluate their efficiency on real-world cases. In order to do so, we introduce methods to evaluate the efficiency of strategies. We also explore the bias that different measurement strategies may induce.
Ten weeks in the life of an eDonkey server
Frédéric Aidouni, Matthieu Latapy and Clémence Magnien
Sixth International Workshop on Hot Topics in Peer-to-Peer Systems (Hot-P2P 2009), May 29, 2009, Rome, Italy
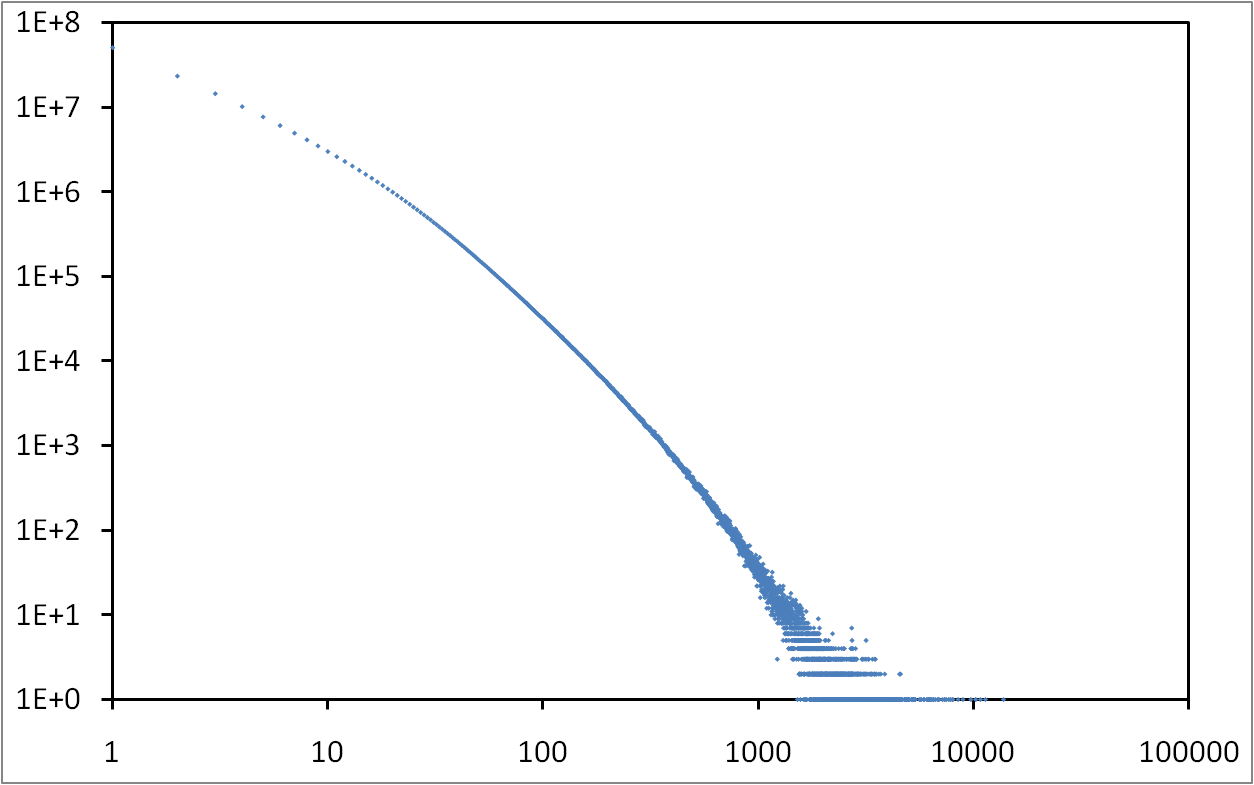
This paper presents a capture of the queries managed by an eDonkey server during almost 10 weeks, leading to the observation of almost 9 billion messages involving almost 90 million users and more than 275 million distinct files. Acquisition and management of such data raises several challenges, which we discuss as well as the solutions we developed. We obtain a very rich dataset, orders of magnitude larger than previously avalaible ones, which we provide for public use. We finally present basic analysis of the obtained data, which already gives evidence of non-trivial features.
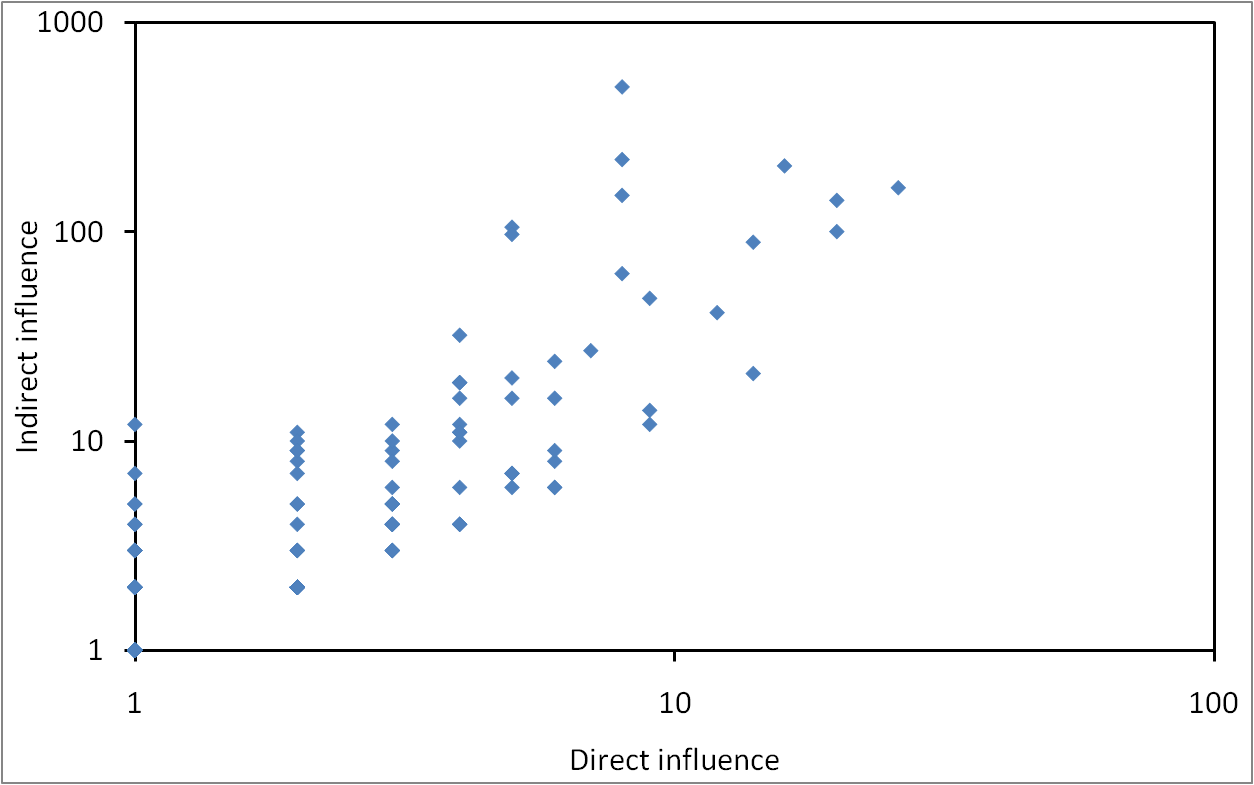
Direct and indirect influence of blogs
Dynamics of the internet topology around me
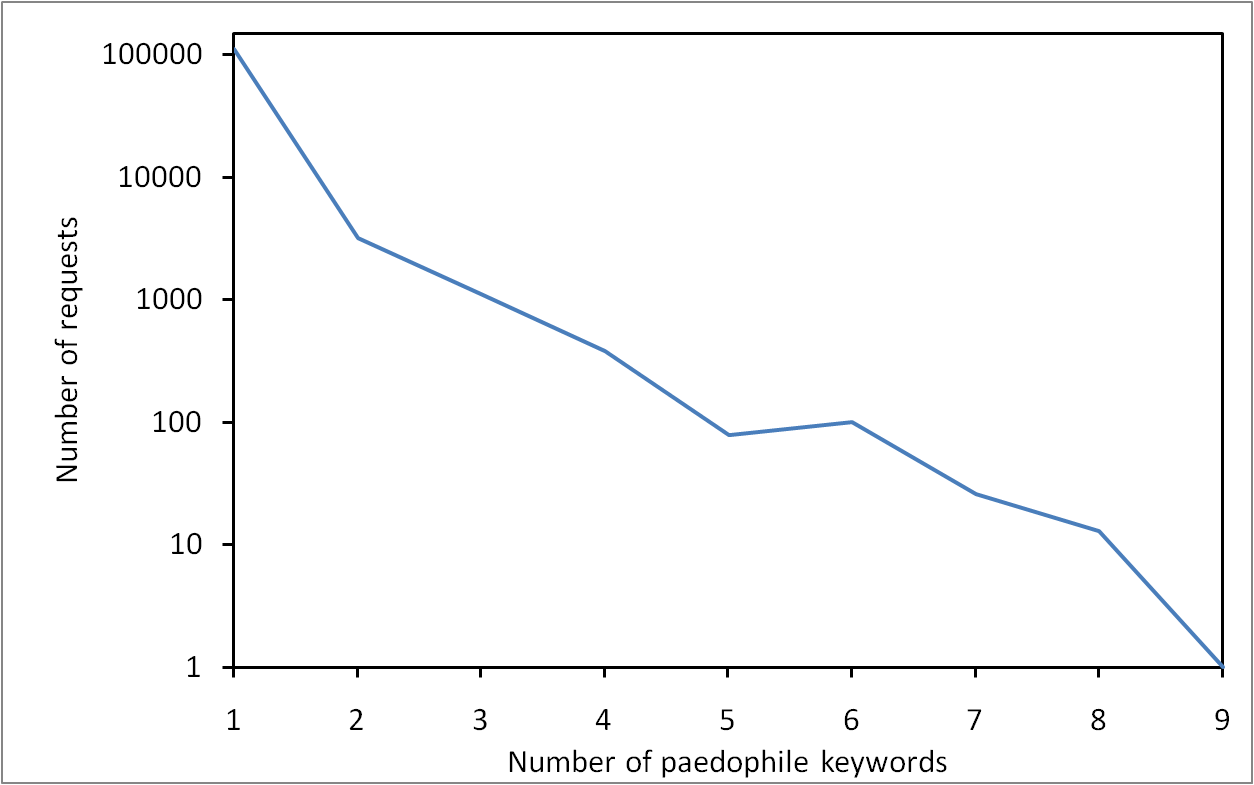
Paedophile keywords in eDonkey queries
Dynamics and stability of communities
Profiles of BFS to model internet topology measurements
Life duration of peers in a P2P system
Stability of community detection
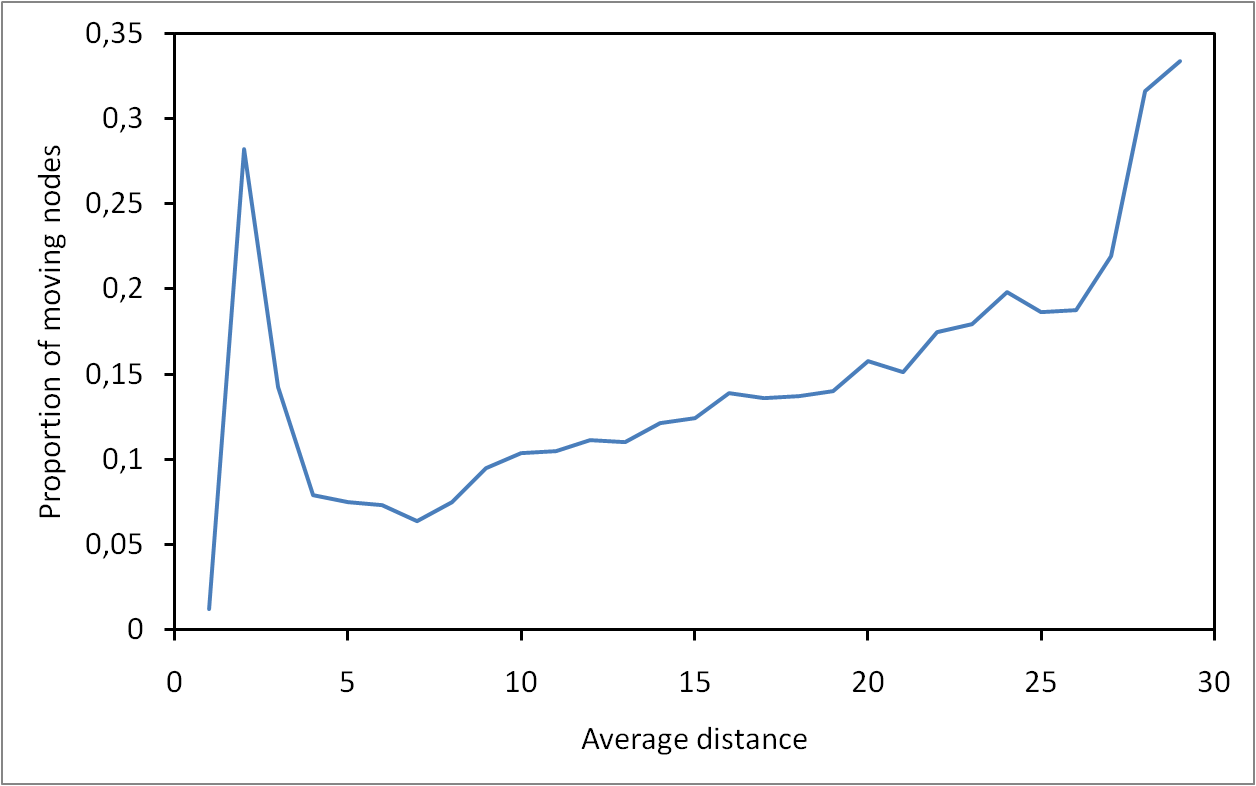
Moving nodes along routes
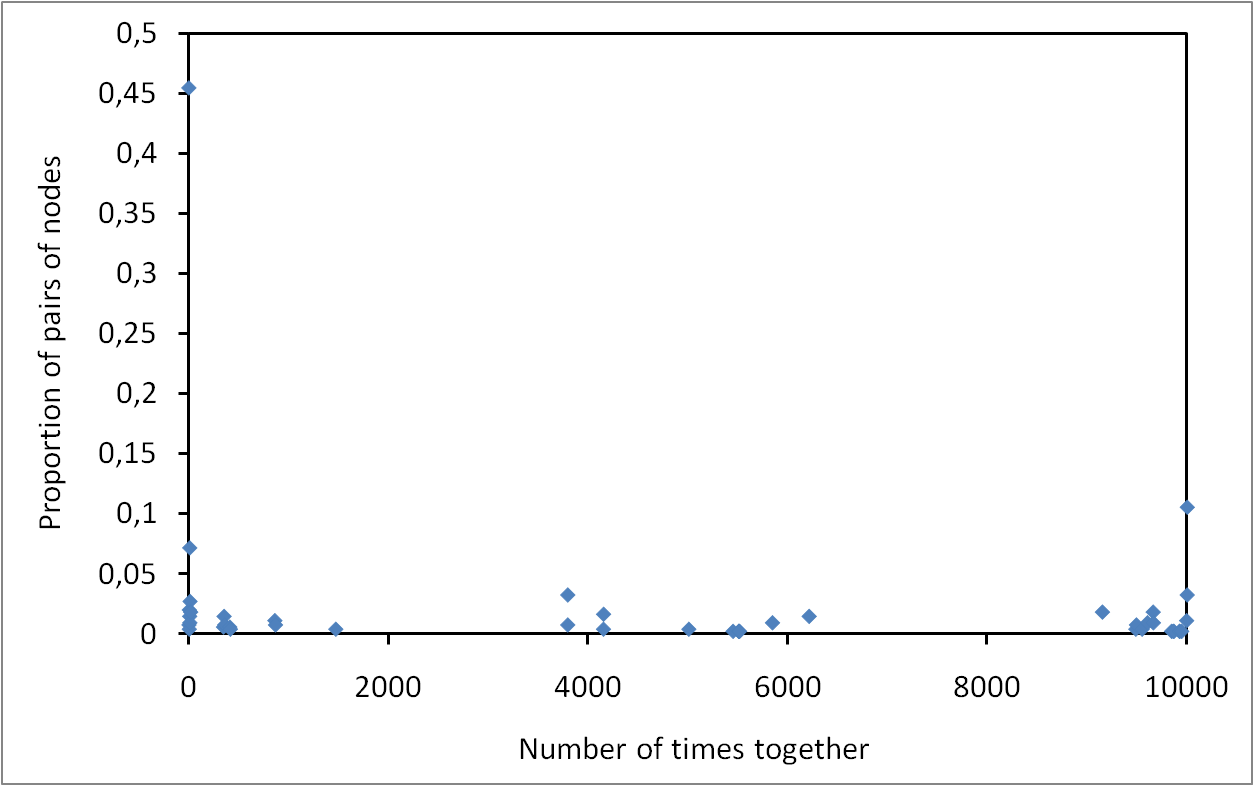
Occurrences of nodes as the measurement duration grows
Efficient Measurement of Complex Networks Using Link Queries
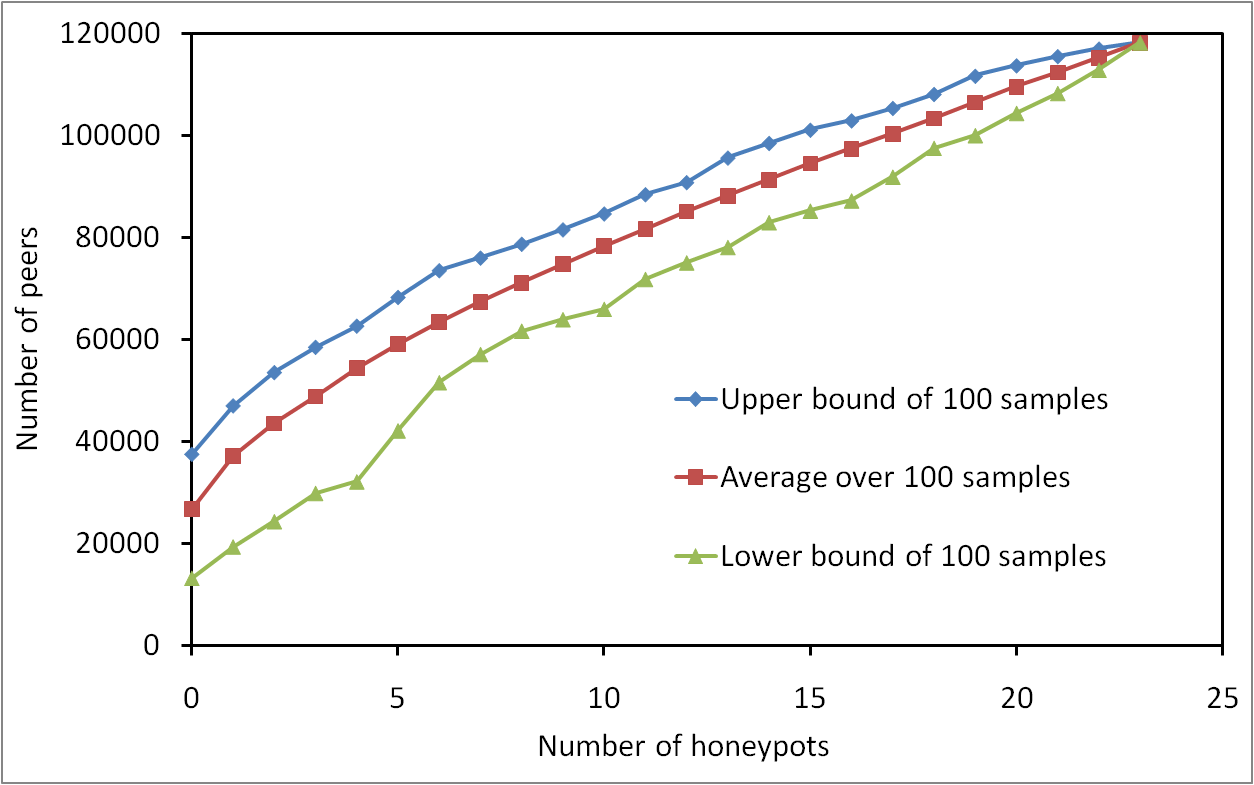
Measurement of eDonkey Activity with Distributed Honeypots
Files diffusion in a edonkey P2P system
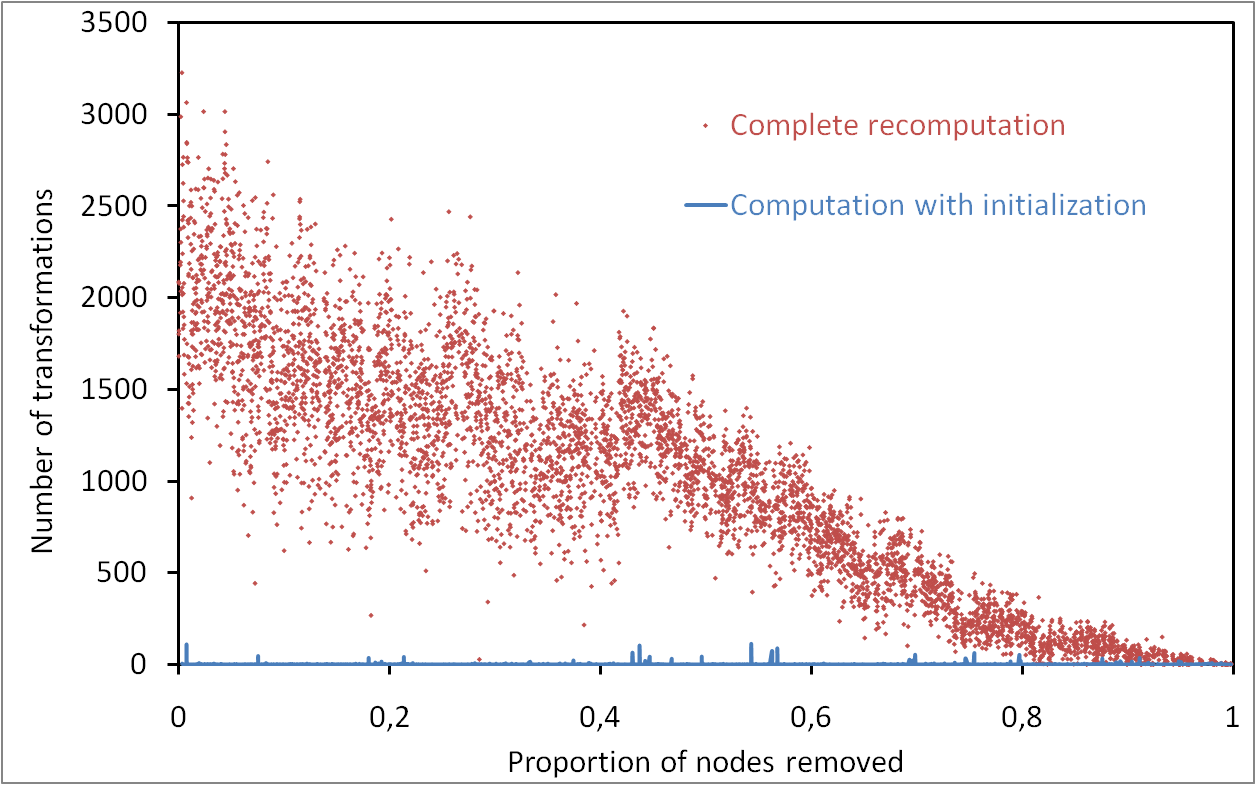
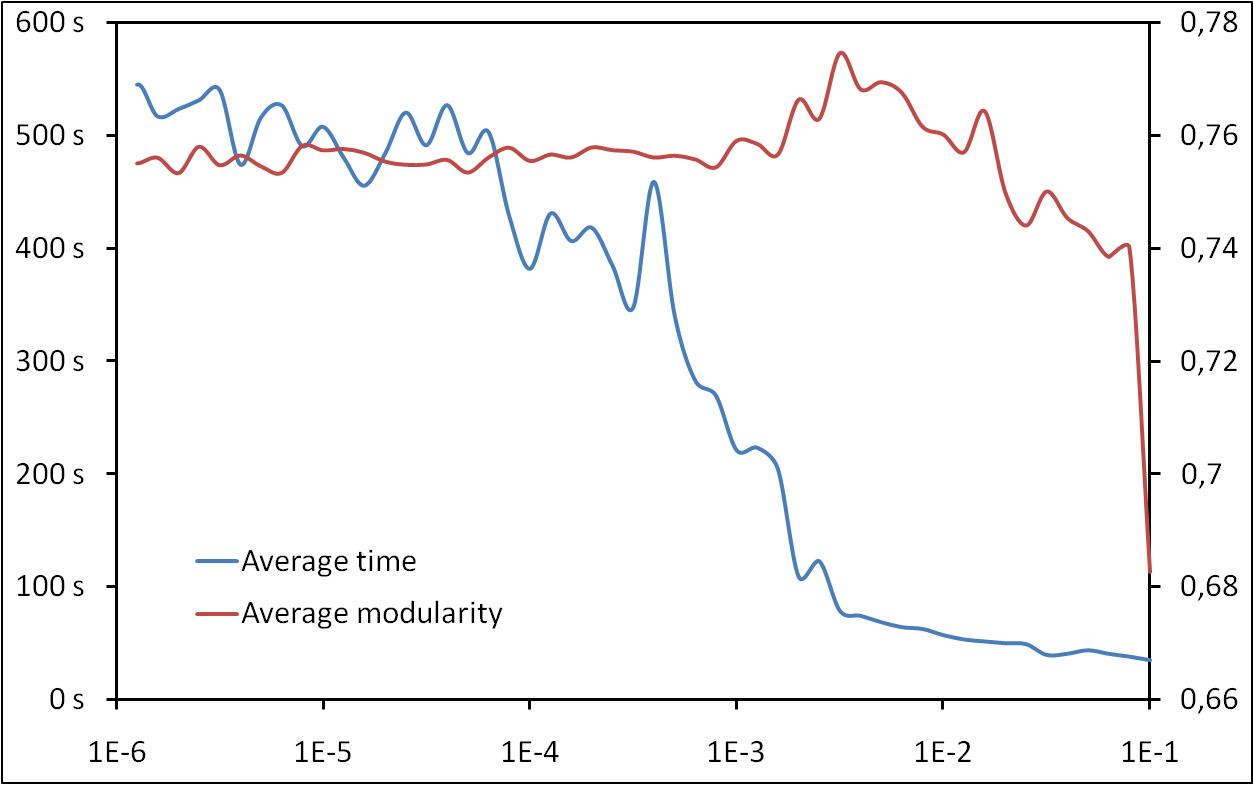
Maximizing modularity: time VS. quality
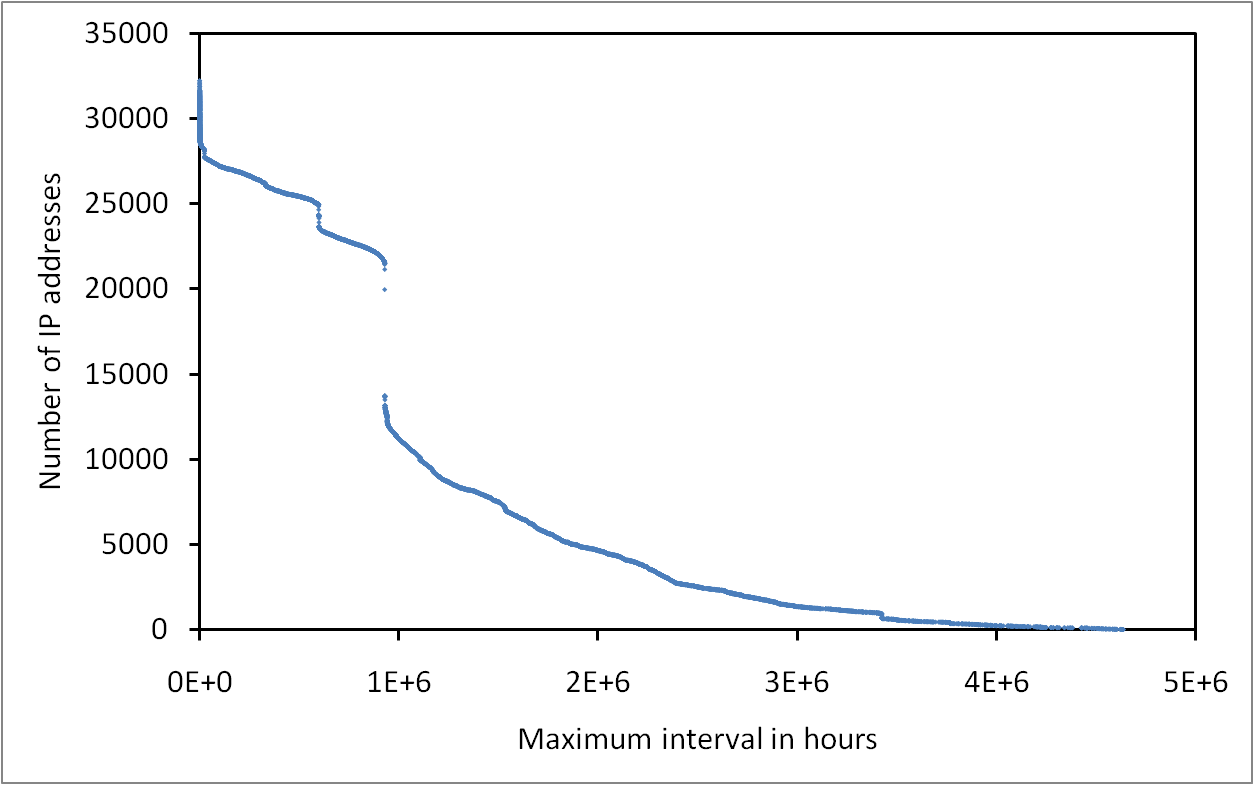
Fast dynamics in Internet topology: preliminary observations and explanations
Clémence Magnien, Frédéric Ouedraogo, Guillaume Valadon, Matthieu Latapy
Fourth International Conference on Internet Monitoring and Protection (ICIMP 2009), May 24-28, 2009, Venice, Italy
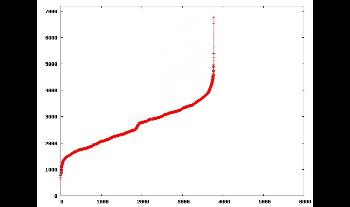
By focusing on what can be observed by running traceroute-like measurements at a high frequency from a single monitor to a fixed destination set, we show that the observed view of the topology is constantly evolving at a pace much higher than expected. Repeated measurements discover new IP addresses at a constant rate, for long period of times (up to several months). In order to provide explanations, we study this phenomenon both at the IP, and at the Autonomous System levels. We show that this renewal of IP addresses is partially caused by a BGP routing dynamics, altering paths between existing ASes. Furthermore, we conjecture that an intra AS routing dynamics is another cause of this phenomenon.
Measurement of eDonkey Activity with Distributed Honeypots
Oussama Allali, Matthieu Latapy and Clémence Magnien
Sixth International Workshop on Hot Topics in Peer-to-Peer Systems (Hot-P2P 2009), May 29, 2009, Rome, Italy
Collecting information about user activity in peer-to-peer systems is a key but challenging task. We describe here a distributed platform for doing so on the eDonkey network, relying on a group of honeypot peers which claim to have certain files and log queries they receive for these files. We then conduct some measurements with typical scenarios and use the obtained data to analyze the impact of key parameters like measurement duration, number of honeypots involved, and number of advertised files. This illustrates both the possible uses of our measurement system, and the kind of data one may collect using it.